

Kapolcs Nagy
Leyla is a Customer Success Specialist at Preline and spends her time speaking to in-house recruiters all over the world.
- 4 min read
Zero-Knowledge Group Membership Management With the Semaphore v4 Protocol
Explore the world of zero-knowledge protocols with Semaphore v4, a powerful tool for anonymous group membership and signaling.

Semaphore is a zero-knowledge protocol that enables anonymous group membership proof and signaling. It's a powerful tool used in various applications, including anonymous voting systems, privacy-preserving financial transactions, and identity verification projects like WorldCoin. In this article, we'll explore the technical aspects of Semaphore v4, breaking down its core components and functionality.
The Basics of Semaphore v4
At its core, Semaphore v4 allows users to prove their membership in a group and send signals anonymously. The protocol is built on several key components:
- Identity Creation
- Group Membership
- Zero-Knowledge Proofs
- Anonymous Signaling
Let's dive into each of these components in detail.
1. Identity Creation
In Semaphore v4, user identities are created using the EdDSA (Edwards-curve Digital Signature Algorithm) scheme. This is a significant change from previous versions and provides more versatility for identity usage.
const { Identity } = require("@semaphore-protocol/identity")
const identity = new Identity(edDSAPrivateKey)
The identity object contains two key components:
- A private key (called the identity secret)
- A public key (called the identity commitment)
The identity commitment is derived from the private key using EdDSA, ensuring that it's computationally infeasible to derive the private key from the public commitment.
2. Group Membership
Groups in Semaphore v4 are managed using a Lean Incremental Merkle Tree (LeanIMT). This data structure efficiently stores and proves membership for large sets of identity commitments.
const { Group } = require("@semaphore-protocol/group")
const group = new Group()
group.addMember(identity.commitment)
When a member is added to a group, their identity commitment is inserted as a leaf in the Merkle tree. The root of this tree represents the current state of the group.
3. Zero-Knowledge Proofs
Semaphore v4 uses zero-knowledge proofs to allow users to prove statements about their identity and group membership without revealing any specific information. The circuit for generating these proofs includes several key components:
- Identity Nullifier: A private value known only to the user.
- Identity Trapdoor: Another private value that, combined with the nullifier, forms the identity secret.
- Merkle Tree Proof: Demonstrates that the user's identity commitment is part of the group's Merkle tree.
- External Nullifier: A public input that can be used to prevent double-signaling.
- Signal: The actual data being transmitted anonymously.
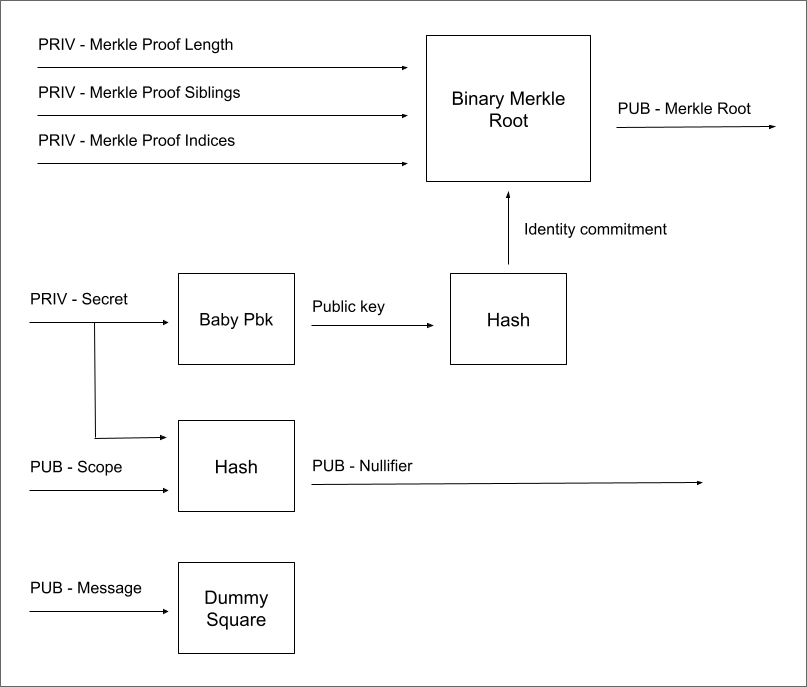
This diagram illustrates the key components and processes in Semaphore v4:
-
Identity Creation:
- PRIV - Secret: The user's private key, used to generate the public key.
- Baby Pbk: Generates the public key from the secret.
- Hash: Creates the identity commitment from the public key.
-
Group Membership:
- Binary Merkle Root: Represents the group, with identity commitments as leaves.
- PRIV - Merkle Proof Length, Siblings, Indices: Private information used to prove membership in the group.
-
Nullifier Generation:
- PUB - Scope: Public information that defines the context of the proof.
- Hash: Combines the secret and scope to create a unique nullifier.
-
Message Handling:
- PUB - Message: The public message or signal being sent.
- Dummy Square: A placeholder operation, possibly for message processing or encryption.
-
Proof Outputs:
- PUB - Merkle Root: The public root of the Merkle tree, representing the current state of the group.
- PUB - Nullifier: A unique identifier for this proof, preventing double-signaling.
This scheme demonstrates how Semaphore v4 maintains privacy while allowing users to prove group membership and send signals. The use of hashes and Merkle trees ensures that no private information is revealed during the process.
4. Anonymous Signaling
The process of anonymous signaling in Semaphore v4 involves generating a zero-knowledge proof that demonstrates the following:
- The user knows the private key corresponding to an identity commitment in the group.
- The user is generating a unique signal for a specific external nullifier.
Here's how you might generate a proof in Semaphore v4:
const { generateProof } = require("@semaphore-protocol/proof")
const externalNullifier = 1234 // This could be a unique identifier for a specific voting event
const signal = 1 // This could represent a "yes" vote
const fullProof = await generateProof(identity, group, externalNullifier, signal)
Verifying Proofs
Once a proof is generated, it can be verified without revealing any information about the identity of the prover:
const { verifyProof } = require("@semaphore-protocol/proof")
const isValid = await verifyProof(fullProof)
If the proof is valid, we know that:
- The prover is a member of the group
- The signal is unique for this external nullifier
- The prover has not double-signaled (for the same external nullifier)
Practical Applications
Semaphore v4's capabilities make it suitable for a wide range of applications:
-
Anonymous Voting Systems: Voters can prove they're eligible to vote without revealing their identity, and each voter can only vote once.
-
Whistleblowing Platforms: Users can prove they're part of an organization without revealing who they are, allowing for anonymous reporting.
-
Privacy-Preserving Social Media: Users can prove they're part of a community without linking their posts to their real identity.
-
Decentralized Identity Systems: Projects like WorldCoin use Semaphore to allow users to prove they're unique individuals without revealing personal information.
Conclusion
Semaphore v4 provides a powerful set of tools for managing group membership and enabling anonymous signaling with zero-knowledge proofs. By understanding its core components - identity creation, group membership, proof generation, and verification - developers can leverage Semaphore to build privacy-preserving applications across a wide range of domains.
As privacy concerns continue to grow in our digital world, protocols like Semaphore v4 will play an increasingly important role in balancing the need for verification with the right to privacy.